BLUF: NOT WITHOUT VERIFICATION!
Unlike “tactical comms” or “walkie-talkies” as we called them as kids, HF comms is a lot harder to know who you are talking to. With “walkie-talkies” or “Handi-Talkies” (HTs) as HAMs like to call them, you can usually see who you are talking to or know they are within a 2-mile radius on average. That’s why those bands are called LOS (Line of Sight) and are reserved for team comms where your teammates are likely to be within line of sight.
Today we have encryption layers on DMR that are fairly easy to implement on the VHF/UHF bands preventing “man-in-the-middle intercepts” as well as “spoofing” one of the group member’s station ID. This is all done with digital modes fairly easily in the background without operator input needed, but to be clear, it’s only legal on business bands even though the radios work on the Amateur bands.
Whether you need encryption is another questions all together, but something I would put out there is that “hiding in plain sight” (talking in plain speak code) is less obvious than putting a signal out nobody can read which raises the question and interest level in “why is this signal so important it needs encryption?”
HF ANALOG SIGNALS
We can get traffic from across the region or nation most days even when propagation is poor if we use “weak signal” digital modes and programs like JS8Call or VaraAC, but there is no encryption allowed by FCC rules on the standard HAM bands so everything you transmit is “in the open” for SIGINT (Signal Intelligence) gathering and malicious injection of misinformation.
With voice (SSB) we can learn a person’s inflections while they talk if we listen to them over a long period of time, I know many NCS’ (Net Control Stations) by their voice on my local Oregon Emergency Net having done nightly check-ins for years, but voice is rarely an option when commercial power is not available to run the 100+ watt radios and amps needed to get the message through in poor propagation conditions.
DIGITAL HF SIGNALS
If you are running digital modes or “keyboard to keyboard” comms, there is nothing to use as positive ID of a particular station, you only get what the user entered into the software as his ID.
So how do you know who you are talking to on HF?
I’ve been seeing more and more ILLEGAL callsigns in the weak signal realm in the past few years, and bogus grid locations being entered into software like JS8Call by the end user also.
I can be broadcasting as PNW1MM from grid DN67 (North Dakota) and nobody can tell the difference between what I tell the program and where I really am broadcasting from. That’s a problem when regular comms are down, and if information where to be purposefully obfuscated.
“Fake News” doesn’t just apply to Twitter and Facebook.
WORK YOUR SOURCES NOW
The whole point of setting up an HF support groups in these “normal” days is that your will have information sources around the nation that can provide reliable “first person” reporting.
But how do I know that the person in my established group is the same one transmitting any given message? Is it because I recognize his callsign? Because he follows the same on-air pattern I am accustomed to?
ALTERNATE CALLSIGNS?
Groups like AmRRON have “tactical callsigns” for their members to use when it’s illegal to transmit or not prudent to use an FCC callsign that is connected to your house address. Please use a POB when applying for your FCC callsign, the farther away from your QTH, the better!
Transmitting as “PIRATE007” means nothing to me though, because even though I have a list of fellow “operators” as a “core member” in the PAID section of the AmRRON Corps website (so does anyone paying them $40), the issue of making a positive ID is the same…
There is still no way to confirm the person transmitting is who we think he is without a pre-existing “challenge / pass” system in place.
CHALLENGE / PASS
A challenge and pass authentication scheme must be established before an event would require it. Think of the old war movies when someone comes up against the camps outer perimeter and is challenged by a sentry.
Sentry challenges with “Flash”, incoming responds “Thunder” and sentry allows them to come forward for further verification. They are still suspected of being the enemy, but they got past the first layer of security. If they come up to the sentry and start speaking Russian instead of English, then there is a problem.
How do we make sure we are speaking to who we think in digital modes? We start with an authentication scheme.
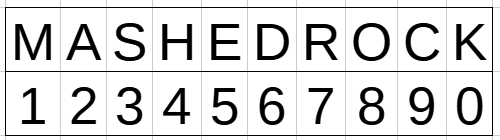
We can use “code” like HETEROGRAMS to issue challenges that are unsecured charactor/number combinations like AmRRONs “MASHEDROCK” listed in the back of their paid version of their SOI.
The challenge is issued as: “What is the SUM of Alpha and Hotel?”
Answer: “Delta” (2+4)
While weak, it means that the person you are talking to has at least a cursory knowledge of your organization (AmRRON in this case) and for non-secure comms, is probably enough to pay attention and trust the traffic being sent if it’s generic news.
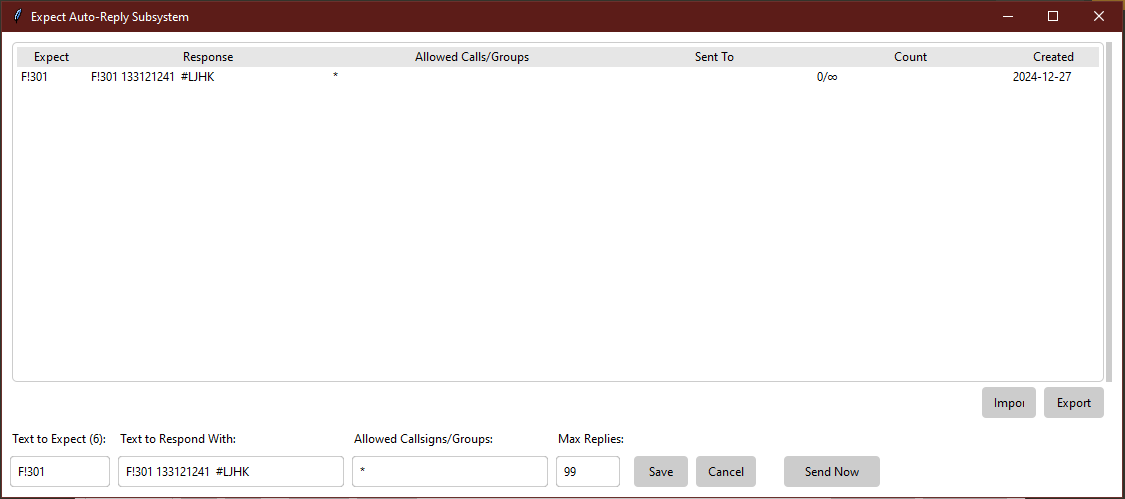
JS8SPOTTER CUSTOM FORMS
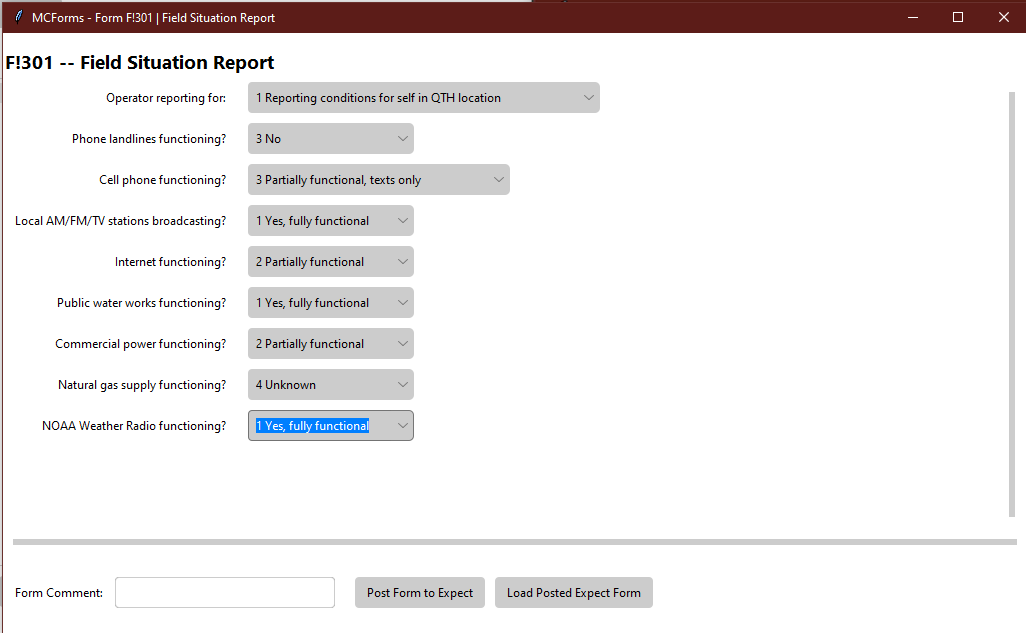
Using JS8Spotter and it’s form function, you can send obscured messages in the “form” of a form, that the receiving station has to have on their system to “decode” the meaning of the data received. The beauty of the system is you can make your own custom forms to use a challenge / pass system. An example using a standard F!301 form is given below.
Over the air you see only “F!301 133121241 #LJHK” transmitted and unless you have the corresponding F!301 form on your system it will not match up to the information sent.
In this case it does, but making a custom form would allow you to add additional information to your liking. Like a sudo CAPTCHA using fields called “Operator First Name” and “Operator Callsign” that have to match up by the selections they send.
If the name is “Joe” and he is #6 of a list of 10 possibilities and his callsign is “K7BVD” and it’s #2 of a list of 10 possibilities, then depending on where the question is in the form (say the first 2 questions in this example) only “F!301 62xxxxxxxxxx” would be a valid message and would be assumed to be from JOE K7BVD.
The operator authentication is just one part of a custom form, all the questions you put on it will only make sense if the sending party has it also.
ENCRYPTION
Eventually we may need parts if not the whole message to remain private between the intended parties and that brings us to using encryption on the message. Using encryption allows us to forgo the challenge/pass stage as the ability to decrypt is only available with the messages intended party.
Sensitive items like those found in a SALUTE report would be better encrypted so the group you are doing the SALUTE report on does not know you are observing them when passing that info up the “food chain”, if one exists, or to others in the area affected by them if it doesn’t.
Picture yourself reporting on Chinese troops that just got activated on US soil, you know, the ones that have been flooding the Mexican border for the past four years at a rate of 10K per day?
If transmission is illegal and or possible interception of the message is highly likely, then transmissions must be short encrypted bursts over the airwaves and never from the same spot, preferably far away from your AO and preferably while moving.
If conditions have become this restricted though, sending HF messages are likely the least of your problems. Encrypting the message is even less of a worry as a state actor (ours, China, or other) will likely DF you and “shoot the messenger” without caring what the message was if HF traffic sources are being hunted.
But there maybe times in between normal life and this extreme example when encrypted messages are warranted. I’ll leave that for you to decide.
Before you get wrapped around the axle on this, consider the following…
We are talking about a possible (likely) point in history when the USA will not have infrastructure for comms. A bureaucracy (if it’s still around) and its rules will be the last thing on your mind during the scenario that would require encrypted messages to be transmitted.
PLANT THE SEED
DISCLAIMER: I’m not an encryption guy and maybe all wet here, but below is my best attempt at it. Please correct me in comments if what I’m saying is completely wrong here.
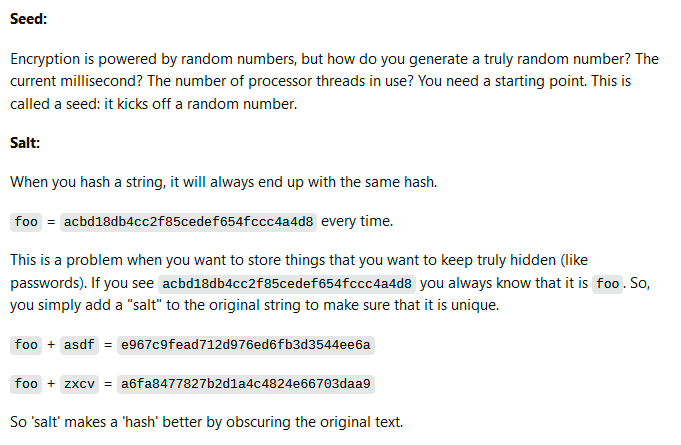
The thing about encryption as I understand it, is that you need to establish your “seed” and mode (AES256 for example) BEFORE you need to use it. Otherwise, you have to send your encryption seed by foot or over the air unencrypted, which obviously defeats the purpose.
Being able to replace your encryption “seed” on the fly after SHTF is pretty hard to do, but you can plan for the compromised scenario by using a “revolving” encryption “hash” by adding a daily “salt” to the seed.
If one hash is compromised (meaning the encryption “hash” is reverse engineered somehow) then by using an additional “salt” that is easy to remember or formed off a revolving pattern, you get a different “hash” or encryption result with each day, making it possible to secure the message again.
Remember, if a state actor is working your encryption this might break it, but then again, if a state actor is on your tail, they will DF you long before caring to decode your message.
Literally “shooting the messenger” is easier than understanding what he is saying.
To me a standard like AES256 which is common in most encryption packages and thought to be un-crackable today would be the best route to take.
With a simple base phrase “seed” and the use of a “salt” to change it up would make the most sense to me.
The succeeding “seeds” could be a phrase with the date added to it each time… An example might look like this:
“NOW IS THE TIME FOR ALL GOOD MEN TO COME TO THE AIDE OF THEIR COUNTRY 12.14.24”
Were the date added changes the encryption “seed” and resulting “hash” daily.
Obviously you want something a little more abstract than a well known typing test as your base phrase and a date stamp for a salt, but you get the point.
If I sent your a message like below on 01.06.25, could you decode it based on what you just read?
J]cfnLvxd2Jh4dZR5rkgxDFe0xnbWWi)2kjuU26LULW3z]4XsXIef4Ju)wuoZeynynl8c]YD4TgU3jsUJ5fOOC7RsuP)GoEpqpSPwgSk6]v5PLtzC8rLYJTJgdBqvP5fYdA4kk73xCmIGBz0MA!
PLAN FOR THE BEST AND HOPE FOR THE BEST?
Should we just forget about authentication and encryption and hope that the guy speaking to us is legit?
Should we consider information passed via HF to be from fellow HAMS and discount the possibility of misinformation on the airwaves?
Should we consider HF to be worthless information or disinformation in SHTF?
HF has gotten information in and out of nations like Cuba when they were being jammed and was a critical path for traffic during WWII via CW operators behind enemy lines even while being actively hunted by the NAZI party using DF equipment.
But do you as a private citizen need to consider securing your message in SHTF?
Maybe, but probably not. Better to have a plan and not need it than to not have a plan and need one IMO.
WHO DO YOU TRUST?
Do you believe anything you hear on the airwaves now? Kind of a trick question as most of what you hear is “rag chewing” or BSing and weather reports, so it doesn’t have much impact on your situation.
We don’t get our “important” information from HF radio in normal times, we get it by the million influencers on Social Media, alternate news outlets on the internet, or official state propaganda from legacy news outlets like CNN. We don’t assume they are telling us the truth and check them against many other sources on the internet before forming an opinion of the matter. When there is only one source for information, the need for trust in the sender is exponentially higher.
A trusted sources is a verifiable source!
WHAT ABOUT WHEN THOSE “NEWS” SOURCES ARE GONE?
HF will become a lot more important and a way to verify the information’s source a a lot more important.
Currently, there are many organizations being created at the grass-roots level for such a time as described, who’s purpose is to keep it’s members informed with solid INTEL during information blackouts that are likely to ensue after an event.
If you have a rapport with the sender of information on HF, meaning you have worked his station many times and know a little background about them, with a simple challenge/pass setup you can probably be sure who they are using a simple HETEROGRAM system like the one in my PNW-MM EMCOMMS BOOK that has 31 of them and the use of which is based on the day of the message being sent. The likelihood of someone having that list before an event and wanting to use it to impersonate someone talking to me is about NILL.
If you are reading this and might ever send traffic in a SHTF even to the @PNW net on JS8Call, you should download that book now. It’s a simple and effective means to prevent against 99.9% of spoofing attempts as very few are going to download that book from this website to be able to pass the daily challenge from it.
Anyway, it’s been an interesting throught experiment, but in the end I think HF in a grid-down scenario will be nothing more than a tool for misinformation to the masses that have no way of confirming the data being passed. I see “Voice of America” being broadcast in our own nation as a “trusted” source for the masses because it’s the “Voice of America” and we all trust name brands, right?
Outside of dedicated groups that practice passing traffic in austere conditions, it’s not going to be worth much. I suggest such a group. Knowledge is power!



Encryption - with computers, public key encryption systems are practical. If you aren't familiar with that tech, please give it a look. These make key exchange simple, as what is needed to *send* you a message can be completely public. There's still a question of an initial authentication, but there are several schemes for that, too. After the initial authentication, the system makes later authentication easy, it also offers non-repudiation for both encrypted and for clear-text messages by signing messages.
Hey PWN Minuteman, this is an excellent, well-thought-out presentation on Comms in a non-permissive environment. And, as one of the majority who are not well acquainted with the technical aspects of radio comms, I really appreciate the time you devoted to sharing all these points for consideration. Lord willing, our nation’s many enemies - foreign and domestic - will be thwarted in every effort by those of us willing and prepared to stand the watch.